Overview
The Crunch protocol must ensure the confidentiality and integrity of submitted models through a robust security framework. As our use cases expand and client demands evolve, we will adapt and enhance the protections to meet the specific requirements of each vertical while maintaining a trustless and transparent environment for all participants. We are implementing and evaluating a combination of techniques, including Trusted Execution Environments (TEE), Multi-Party Computation (MPC), enabling Crunchers to run their own nodes and other privacy-preserving techniques to safeguard model ownership and ensuring coordinators can maintain data privacy.Trusted Execution Environments (TEE)
In cooperation with Phala Network we implemented the ability of Model Runners to run on their own Trusted Execution Environments (TEE) to ensure the confidentiality and integrity of submitted models. This solution is currently in the late stages of testing and should be available in the near future.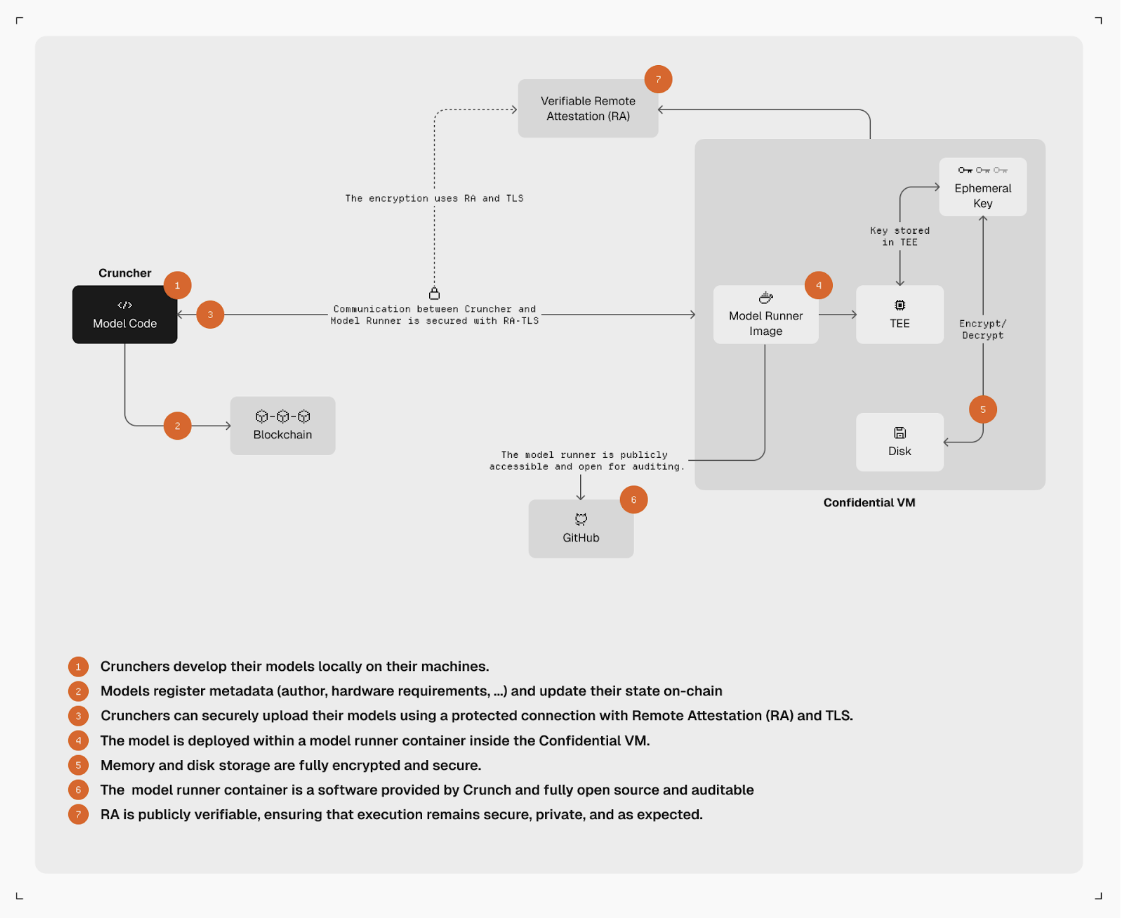
TEE Architecture Overview
Multi-Party Computation (MPC)
In cooperation with Arcium we are exploring the use of Multi-Party Computation (MPC) to ensure the confidentiality and integrity of submitted models. This solution is currently in the early stages of development and should be available in the near future.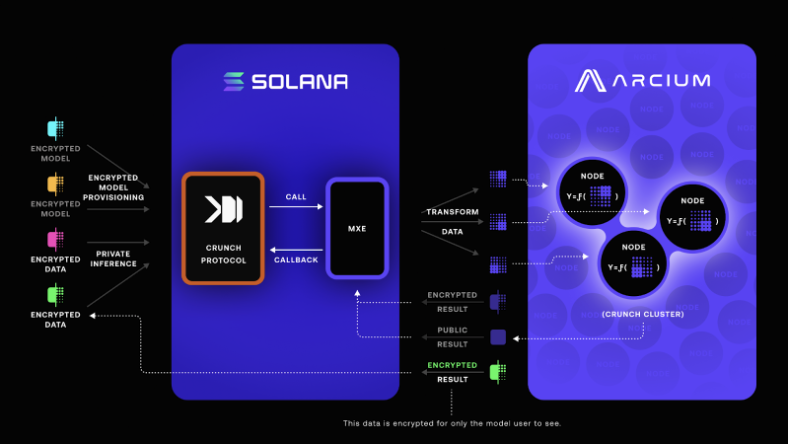
MPC Architecture Overview